Essential Security Technologies: Visualizing the Modern Defense Ecosystem
Understanding the evolving landscape of security technology integration
I've been tracking the rapid evolution of security technologies from siloed systems to fully integrated ecosystems. Today, I'll guide you through the essential technologies that modern security teams need to effectively protect their organizations against evolving threats.
The Evolving Security Technology Landscape
I've witnessed firsthand how security technology has undergone a dramatic transformation over the past decade. What was once a collection of disconnected, siloed systems has evolved into sophisticated, integrated ecosystems that provide comprehensive protection across physical and digital domains.

Key Drivers of Modern Security Technology Adoption
- Increasing sophistication and frequency of cyber threats
- Growing regulatory compliance requirements across industries
- Need for operational efficiency and cost optimization
- Shift toward remote work and distributed operations
- Integration of physical and digital security domains
Security Technology Adoption by Industry
The following chart shows the varying rates of advanced security technology implementation across key industries:
As threats continue to evolve, I've found that security teams need better ways to visualize these complex landscapes. This is where technology industry insights become invaluable. PageOn.ai's visualization tools help security professionals map threat vectors, understand technology relationships, and identify potential vulnerabilities in a clear, intuitive format.
Core Technology Components for Comprehensive Security
In my experience, building a robust security technology stack requires careful consideration of both physical and digital security components. Let's explore the essential technologies that form the foundation of a comprehensive security program.
Security Technology Ecosystem
The modern security technology stack consists of three interconnected domains:
flowchart TD
subgraph Physical["Physical Security Domain"]
Access["Access Control Systems"]
Video["Video Surveillance"]
Intrusion["Intrusion Detection"]
Environ["Environmental Monitoring"]
end
subgraph Digital["Digital Security Domain"]
Firewall["Firewalls & Network Security"]
EDR["Endpoint Detection & Response"]
Encrypt["Data Encryption"]
Cloud["Cloud Security Services"]
end
subgraph Integration["Integration Platforms"]
SIEM["Security Information Management"]
Unified["Unified Control Interfaces"]
API["API Ecosystems"]
end
Physical --> Integration
Digital --> Integration
Integration --> Analysis["Analytics & Intelligence"]
Physical Security Technologies
Access Control Systems
Modern access control has evolved from simple key cards to sophisticated biometric solutions that integrate with other security systems. These technologies provide granular control over who can access specific areas and when.
Video Surveillance
Today's video surveillance systems feature high-resolution IP cameras with advanced analytics capabilities, enabling automatic detection of suspicious activities and seamless integration with access control systems.
Intrusion Detection
From motion sensors to glass-break detectors, these systems form a critical layer of physical security, alerting teams to unauthorized access attempts.
Environmental Monitoring
Systems that detect environmental threats like fire, water, and temperature fluctuations protect both physical assets and the technology infrastructure itself.

Digital Security Infrastructure
The digital security landscape has grown increasingly complex. An integrated system approach is essential for effective protection. Key components include:
| Technology | Function | Integration Benefits |
|---|---|---|
| Firewalls | Control network traffic based on security rules | Provides context to SIEM systems, coordinates with EDR |
| EDR Systems | Monitor endpoints for suspicious activities | Feeds threat intelligence to central management platforms |
| Data Encryption | Protects sensitive information from unauthorized access | Works with access control to ensure proper data handling |
| Cloud Security | Protects cloud-based assets and enables remote operations | Extends security perimeter beyond physical locations |
Integration Platforms: The Critical Connective Tissue
In my work with security teams, I've found that integration platforms are what transform individual security technologies into a cohesive ecosystem. These platforms include:
- Security Information Management Systems: Aggregate and correlate data from multiple security sources
- Unified Control Interfaces: Provide single-pane-of-glass visibility across security domains
- API-Driven Ecosystems: Enable custom integrations between various security technologies
Using PageOn.ai's AI Blocks feature, security architects can model their security system architecture to identify potential gaps and visualize how different components interact. This approach helps teams build more resilient security ecosystems by ensuring comprehensive coverage across all potential threat vectors.
The Intelligence Layer: Making Security Data Actionable
Modern security technologies generate enormous volumes of data. The true value comes from transforming this data into actionable intelligence that enables proactive security measures and efficient incident response.
Artificial Intelligence and Machine Learning Applications

I've seen firsthand how AI and ML technologies are revolutionizing security operations. These technologies enable:
Behavior Pattern Recognition
AI systems establish baselines of normal behavior and automatically flag deviations, enabling early detection of potential threats before they escalate.
Predictive Threat Analysis
Machine learning algorithms analyze historical security data to forecast potential future threats, allowing security teams to implement preventative measures.
Automated Response Workflows
AI-powered systems can trigger predefined response protocols for common security events, reducing response time and ensuring consistent handling.
As AI tool trends 2025 continue to evolve, we'll see even more sophisticated applications of artificial intelligence in security operations. These advancements will enable security teams to manage increasingly complex threat landscapes with greater efficiency.
Data Analytics for Security Operations
Security Data Analytics Value Proposition
Understanding the relative impact of different analytics capabilities:
Effective security analytics platforms provide:
- Real-time monitoring dashboards that provide at-a-glance visibility into security status
- Threat intelligence integration that incorporates external data sources to enhance threat detection
- Compliance and reporting tools that streamline regulatory requirements
PageOn.ai's Deep Search capabilities help security teams visualize complex security data relationships, making it easier to identify patterns and connections that might otherwise go unnoticed. This visual approach to security analytics helps teams make better decisions faster, especially during critical security incidents.
Mobile and Remote Security Management
The days of security teams being tethered to control rooms are long gone. Modern security operations require mobile capabilities that enable teams to monitor and respond to incidents from anywhere.
Evolution of Security Monitoring
The shift from static to mobile security operations:
flowchart LR
A[Traditional CCTV Room] -->|Limited Mobility| B[Networked Monitoring]
B -->|Remote Access| C[Web-Based Dashboards]
C -->|Anywhere Access| D[Mobile Security Apps]
D -->|Real-time Collaboration| E[Integrated Mobile Ops]
style A fill:#FFE6CC,stroke:#FF8000
style B fill:#FFD699,stroke:#FF8000
style C fill:#FFC266,stroke:#FF8000
style D fill:#FFAD33,stroke:#FF8000
style E fill:#FF8000,stroke:#FF8000,color:#fff
Essential Mobile Applications for Security Teams

In my experience working with security teams, I've found that the following mobile applications are essential for effective remote security management:
Mobile Video Monitoring
Applications that provide secure access to live and recorded video feeds from surveillance systems, with PTZ (pan-tilt-zoom) control capabilities.
Access Control Management
Apps that allow security personnel to grant or revoke access permissions remotely, and receive real-time alerts about access events.
Incident Response Coordination
Collaborative platforms that enable team communication, task assignment, and status tracking during security incidents.
Security Analytics Dashboards
Mobile-optimized interfaces that provide key security metrics and alerts, enabling data-driven decision making from anywhere.
Secure Remote Access Considerations
While mobile security management offers tremendous benefits, it also introduces new security challenges. I recommend implementing these essential safeguards:
- Multi-factor authentication for all remote access to security systems
- End-to-end encryption for all data transmission between mobile devices and security infrastructure
- Role-based access controls that limit mobile functionality based on user permissions
- Mobile device management (MDM) solutions to enforce security policies on devices used for remote security operations
Using PageOn.ai's visual tools, security teams can create clear workflow diagrams that document mobile security protocols and procedures. These visual guides help ensure consistent implementation of security practices across distributed teams.
Emerging Technologies Reshaping Security Operations
The security technology landscape continues to evolve rapidly. I'm particularly excited about several emerging technologies that are transforming how security teams operate.
Security Automation Technologies

Automation is revolutionizing security operations by handling routine tasks, enabling human security personnel to focus on more complex challenges. Key automation technologies include:
- Security patrol robots that can navigate facilities autonomously, equipped with cameras and sensors to detect anomalies
- Automated threat response protocols that trigger predefined actions based on specific security events
- AI-powered decision support systems that analyze incidents and recommend appropriate responses
Security Automation Adoption Timeline
Projected implementation of automation technologies in security operations:
IoT and Connected Security Devices
The Internet of Things (IoT) is creating new opportunities for security teams to gather data from distributed sensors and devices. Some of the most promising applications include:
IoT Security Architecture
A typical IoT security implementation:
flowchart TD
Sensors["IoT Sensors & Devices"] -->|Data Collection| Gateway["Edge Gateways"]
Gateway -->|Secure Transmission| Cloud["Cloud Platform"]
Cloud -->|Data Processing| Analytics["Analytics Engine"]
Analytics -->|Insights & Alerts| Dashboard["Security Dashboard"]
Dashboard -->|Notifications| Mobile["Mobile Alerts"]
Dashboard -->|Controls| Response["Automated Response"]
subgraph "Physical Environment"
Sensors
end
subgraph "Edge Computing"
Gateway
end
subgraph "Cloud Infrastructure"
Cloud
Analytics
end
subgraph "Security Operations"
Dashboard
Mobile
Response
end
While IoT devices offer tremendous benefits for security operations, they also introduce new security challenges. I always recommend implementing these safeguards:
- Network segmentation to isolate IoT devices from critical systems
- Regular firmware updates to address security vulnerabilities
- Strong authentication mechanisms for device access
- Encryption for all data transmitted by IoT devices
PageOn.ai's visualization tools are particularly valuable for modeling IoT security architectures. By creating visual representations of IoT deployments, security teams can better understand potential vulnerabilities and implement appropriate safeguards.
Building an Integrated Security Technology Stack
Creating an effective security technology stack requires careful planning and a strategic approach. I've developed a framework that helps security teams select and implement technologies that address their specific needs.
Assessment Framework for Technology Selection
Security Technology Assessment Framework
A structured approach to evaluating security technologies:
flowchart TD
Start[Start Assessment] --> Req[Identify Requirements]
Req --> Threat[Threat Analysis]
Threat --> Gap[Gap Assessment]
Gap --> Eval[Technology Evaluation]
Eval --> POC[Proof of Concept]
POC --> Decision{Decision Point}
Decision -->|Proceed| Deploy[Deployment Planning]
Decision -->|Reject| Req
Deploy --> Implement[Implementation]
Implement --> Monitor[Monitoring & Optimization]
classDef orange fill:#FF8000,stroke:#FF8000,color:white
classDef blue fill:#42A5F5,stroke:#42A5F5,color:white
classDef green fill:#66BB6A,stroke:#66BB6A,color:white
class Start,Req,Threat,Gap orange
class Eval,POC,Decision blue
class Deploy,Implement,Monitor green
When evaluating security technologies, I recommend focusing on these key considerations:
Organizational Requirements
- Specific threat landscape
- Compliance requirements
- Operational constraints
- Existing technology investments
Technology Interoperability
- API availability
- Integration capabilities
- Standards compliance
- Vendor partnership ecosystem
Total Cost of Ownership
- Initial acquisition costs
- Implementation expenses
- Ongoing maintenance
- Training requirements
Implementation Roadmap
I've found that a phased implementation approach is most effective for building an integrated security technology stack. This approach typically includes:

- Foundation Phase: Implement core technologies that address the most critical security requirements
- Integration Phase: Deploy platforms that connect and coordinate core technologies
- Enhancement Phase: Add specialized technologies to address specific use cases or threats
- Optimization Phase: Refine configurations and workflows to maximize effectiveness
For organizations building their security technology stack, I recommend starting with essential classroom tech stack tools that can be adapted for security purposes. Many of the visualization and collaboration tools used in educational settings can be repurposed for security planning and training.
PageOn.ai's structured content blocks are particularly useful for creating visual security technology roadmaps. These roadmaps help align stakeholders around implementation priorities and timelines, ensuring that security investments deliver maximum value.
The Human Element: Security Teams and Technology
While technology is essential for modern security operations, I've learned that the human element remains critically important. The most effective security programs strike a balance between technological capabilities and human expertise.

Balancing Technology and Human Expertise
In my experience, the most successful security operations follow these principles:
- Technology augments human capabilities rather than replacing security personnel
- Automation handles routine tasks, freeing human operators to focus on complex problems
- Human judgment remains essential for interpreting alerts and determining appropriate responses
- Technology investments are balanced with investments in personnel development
Training Requirements for Modern Security Technologies
As security technologies become more sophisticated, training requirements have evolved. I recommend developing a comprehensive training program that includes:
Security Team Skills Development
Priority areas for security team training:
Building Effective Security Operations Centers (SOCs)
The modern Security Operations Center (SOC) serves as the nerve center for security technology management. Based on my experience, effective SOCs typically include:
- Integrated technology platforms that provide comprehensive visibility
- Clearly defined roles and responsibilities for SOC personnel
- Documented processes and procedures for handling different types of security events
- Performance metrics that measure SOC effectiveness
- Continuous improvement mechanisms to refine operations over time
PageOn.ai's visualization tools are invaluable for creating clear training materials and operational procedures for security teams. Visual representations of complex security concepts help personnel understand their roles and responsibilities more quickly, improving overall team effectiveness.
Future-Proofing Security Technology Investments
The security technology landscape continues to evolve rapidly. Organizations that want to maximize the return on their security investments need to think strategically about future-proofing their technology choices.
Technology Trends Shaping Security Through 2025 and Beyond
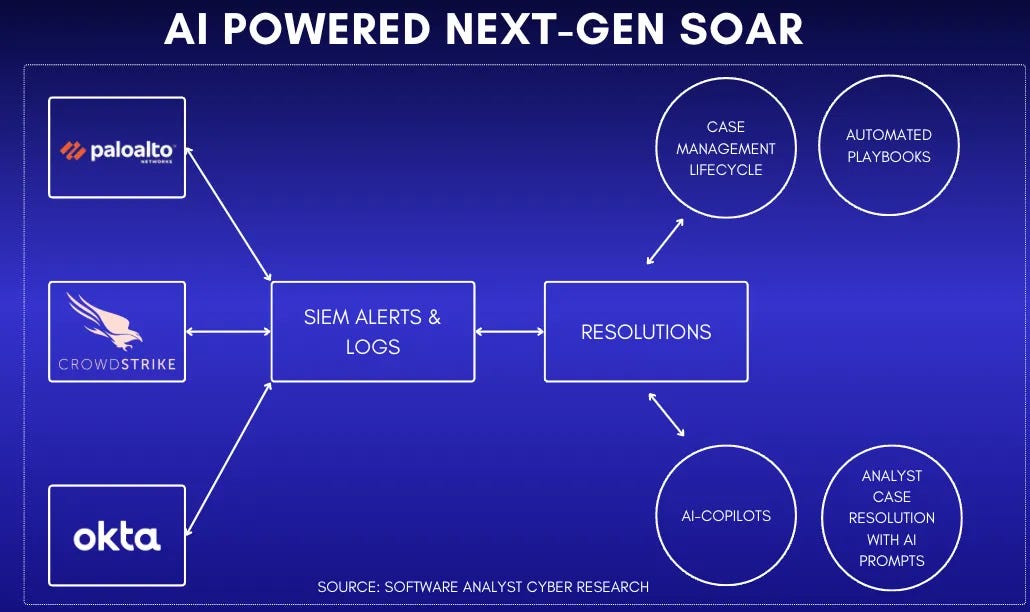
Based on current trajectories and AI tool trends 2025, I anticipate these key developments in security technology:
AI-Driven Predictive Security
Advanced AI systems will move beyond detection to prediction, identifying potential security incidents before they occur based on subtle patterns in data.
Quantum-Resistant Encryption
As quantum computing advances, security technologies will implement new encryption methods designed to withstand quantum-based attacks.
Extended Reality (XR) Security Interfaces
Security teams will use augmented and virtual reality interfaces to visualize and interact with security data in more intuitive ways.
Biometric Authentication Evolution
Biometric systems will become more sophisticated, incorporating behavioral biometrics and continuous authentication methods.
Building Adaptable and Scalable Security Architectures
To future-proof security technology investments, I recommend these architectural principles:
Future-Proof Security Architecture
Key principles for adaptable security design:
flowchart TD
Core["Core Security Platform"] --- API["Open API Layer"]
API --- Apps["Security Applications"]
API --- Data["Data Analytics"]
API --- Future["Future Technologies"]
subgraph "Foundation"
Core
end
subgraph "Integration Layer"
API
end
subgraph "Functional Layer"
Apps
Data
Future
end
style Core fill:#FF8000,stroke:#FF8000,color:white
style API fill:#42A5F5,stroke:#42A5F5,color:white
style Apps fill:#66BB6A,stroke:#66BB6A,color:white
style Data fill:#66BB6A,stroke:#66BB6A,color:white
style Future fill:#66BB6A,stroke:#66BB6A,color:white
- Modular design that allows components to be upgraded or replaced without disrupting the entire system
- Open standards and APIs that enable integration with new technologies as they emerge
- Cloud-based infrastructure that can scale with changing requirements
- Vendor diversity to avoid dependence on a single provider's technology roadmap
Evaluating Emerging Technologies
When evaluating emerging security technologies, I use this assessment framework:
| Evaluation Criteria | Key Questions |
|---|---|
| Strategic Alignment | Does the technology address current or anticipated security challenges? Does it align with the organization's security strategy? |
| Technology Maturity | Is the technology proven in real-world environments? What is the vendor's track record for innovation and support? |
| Integration Potential | How easily does the technology integrate with existing systems? Does it use standard protocols and interfaces? |
| Total Value | What is the expected ROI? Does the technology deliver benefits beyond security (e.g., operational efficiency)? |
PageOn.ai's visual tools help security teams create technology evolution maps that illustrate how their security architecture will evolve over time. These visual forecasts help align stakeholders around a common vision for security technology investments.
Transform Your Security Technology Planning with PageOn.ai
Visualize your security technology stack, create clear implementation roadmaps, and develop compelling training materials that help your team understand complex security concepts.
Conclusion
Building an effective security technology ecosystem requires careful planning, strategic investment, and ongoing adaptation. By focusing on integration, intelligence, and scalability, security teams can create technology stacks that address today's threats while remaining adaptable to future challenges.
Throughout this exploration of essential security technologies, we've seen how visualization tools like PageOn.ai can help security teams better understand complex relationships between technologies, communicate implementation plans, and develop effective training materials. These visual approaches to security planning are becoming increasingly important as security technologies grow more sophisticated and interconnected.
As you develop your organization's security technology strategy, remember that the goal isn't simply to deploy the latest technologies, but to create an integrated ecosystem that enhances your team's ability to protect critical assets. With the right approach to technology selection and implementation, you can build a security program that's both effective today and adaptable to tomorrow's challenges.
I encourage you to explore tools for industry insights that can help you stay informed about emerging security technologies and best practices for implementation.
You Might Also Like
How AI Saves Marketing Teams 5+ Hours Weekly While Boosting Productivity 83% | Visual Content Revolution
Discover how AI transforms marketing workflows, saving 5+ hours weekly and boosting productivity by 83%. Learn visual content strategies that eliminate manual tasks and accelerate campaigns.
How 85% of Marketers Transform Content Strategy with AI Visual Tools | PageOn.ai
Discover how 85% of marketers are revolutionizing content strategy with AI tools, saving 3 hours per piece while improving quality and output by 82%.
Creating Visual AI Ethics Frameworks: A Leadership Guide for Modern Business | PageOn.ai
Discover how to develop comprehensive visual AI ethics frameworks for your organization. This guide helps business leaders translate complex ethical principles into clear visual guidelines.
The Visual Evolution of American Infrastructure: Canals to Digital Networks | PageOn.ai
Explore America's infrastructure evolution from historic canal networks to railroads, interstate highways, and digital networks with interactive visualizations and timelines.
