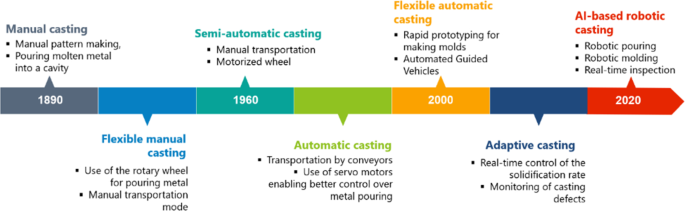
Visualizing the Future: How SOAR Platforms Transform Cybersecurity Response
The Evolution of Security Response Frameworks
In today's rapidly evolving threat landscape, I've witnessed how cybersecurity teams struggle to keep pace with increasingly sophisticated attacks while managing limited resources. SOAR platforms have emerged as a game-changing solution, bringing together orchestration, automation, and response capabilities to transform how organizations handle security incidents.
The Evolution of Security Response Frameworks
I've observed the cybersecurity landscape transform dramatically over the past decade. What once required manual intervention by skilled analysts has increasingly shifted toward automated systems capable of detecting and responding to threats in real-time. This evolution wasn't just a technological preference—it became a necessity.
The challenge facing security operations teams today is stark: while threats continue to multiply in both volume and sophistication, the resources available to combat them—particularly skilled personnel—remain scarce. In my experience working with organizations across industries, I've seen firsthand how this ai response generators gap creates significant vulnerabilities.
Security Orchestration, Automation, and Response (SOAR) platforms emerged as a direct solution to this cybersecurity skills gap. By automating routine tasks and orchestrating complex workflows across multiple security tools, SOAR allows security teams to accomplish more with fewer resources.
The Three Pillars of SOAR
- Security Orchestration: The integration and coordination of various security tools and processes into cohesive workflows.
- Automation: The execution of predefined actions without human intervention, based on specific triggers or conditions.
- Response: The systematic approach to addressing security incidents, from initial detection through resolution and documentation.
As I've implemented SOAR solutions, I've found that understanding these three pillars is crucial for successful deployment. Together, they create a framework that enables security teams to respond to threats more quickly, consistently, and effectively than ever before.
Mapping the SOAR Architecture
When I explain SOAR to stakeholders, I often describe it as the command center for security operations—a central hub where all security activities converge, are coordinated, and executed. To truly understand SOAR's value, we need to visualize how it fits within the broader security ecosystem.
SOAR as the Security Operations Hub
flowchart TD
subgraph "Security Operations Hub"
SOAR["SOAR Platform"]
end
subgraph "Data Sources"
SIEM["SIEM Systems"]
EDR["EDR Solutions"]
FW["Firewalls"]
TI["Threat Intelligence"]
end
subgraph "Response Actions"
CM["Case Management"]
PB["Playbooks"]
RA["Remediation Actions"]
DOC["Documentation"]
end
SIEM --> SOAR
EDR --> SOAR
FW --> SOAR
TI --> SOAR
SOAR --> CM
SOAR --> PB
SOAR --> RA
SOAR --> DOC
style SOAR fill:#FF8000,stroke:#333,stroke-width:2px
Breaking down the components of an effective SOAR implementation reveals several critical elements that must work together seamlessly:
Integration Framework
The connective tissue that links SOAR with other security tools, enabling data exchange and action execution.
Automation Engine
Powers the execution of playbooks and workflows based on predefined conditions and triggers.
Case Management System
Tracks incidents from detection to resolution, maintaining documentation and audit trails.
Analytics & Reporting
Provides insights into security operations performance and effectiveness.
The interconnected workflow between threat intelligence, case management, and response actions forms the backbone of SOAR functionality. When an alert is triggered, the SOAR platform enriches it with threat intelligence, creates a case, and initiates appropriate response actions—all within a unified system.

In my experience implementing SOAR solutions, I've found that PageOn.ai's visualization capabilities are invaluable for creating clear representations of SOAR architecture. These visualizations help stakeholders understand the complex relationships between different security components and how SOAR orchestrates them, making it easier to gain buy-in for security investments.
The Automation Engine: Core Capabilities Visualized
At the heart of any SOAR platform lies its automation engine—the component that executes predefined playbooks and workflows in response to security events. I've found that visualizing these automation capabilities helps teams better understand and leverage their full potential.
SOAR Playbook Execution Flow
flowchart TD
Start([Alert Received]) --> Triage{Automated Triage}
Triage -->|Low Severity| LowPath[Enrich & Document]
Triage -->|Medium Severity| MedPath[Investigate & Validate]
Triage -->|High Severity| HighPath[Contain & Remediate]
LowPath --> Close([Close Case])
MedPath --> Valid{Threat Valid?}
Valid -->|No| Close
Valid -->|Yes| Escalate[Escalate to Analyst]
HighPath --> Contain[Isolate Affected Systems]
Contain --> Remediate[Apply Remediation]
Remediate --> Report[Generate Incident Report]
Report --> Close
Escalate --> Analyst[Analyst Review]
Analyst --> Decision{Action Required?}
Decision -->|No| Close
Decision -->|Yes| Action[Execute Response Action]
Action --> Report
style Start fill:#FF8000,stroke:#333,stroke-width:2px
style Close fill:#66BB6A,stroke:#333,stroke-width:2px
Playbook creation and execution is one of the most powerful aspects of SOAR platforms. In my work with security teams, I've helped develop playbooks for common scenarios such as:
- Phishing email investigation and response
- Malware detection and containment
- User account compromise handling
- Data exfiltration detection and response
- Vulnerability management and patching
Decision trees and conditional response paths are crucial components of these playbooks, allowing for dynamic responses based on the specific characteristics of each security event. For example, a suspicious login attempt might trigger different actions depending on factors such as:

Integration points with existing security infrastructure are what make SOAR truly powerful. By connecting with tools like firewalls, endpoint protection platforms, and email security gateways, SOAR can orchestrate responses across the entire security stack.
When I need to illustrate complex automation sequences to stakeholders or team members, I use PageOn.ai to create dynamic process maps. These visual representations make it much easier to understand the flow of information and actions within the SOAR platform, helping to identify potential gaps or optimization opportunities in our security processes.
The ability to visualize these workflows has been particularly valuable when training new team members or when explaining our security response capabilities to executive leadership. Clear visuals help bridge the gap between technical complexity and strategic understanding.
Integration Ecosystem: Building the Security Mesh
One of the most powerful aspects of SOAR platforms is their ability to integrate with and orchestrate a wide range of security tools. In my experience implementing security automation, I've found that creating a visual representation of this integration ecosystem helps teams understand the comprehensive coverage and capabilities of their security infrastructure.
SOAR Integration Ecosystem
flowchart TD
SOAR((SOAR Platform)) --> SIEM[SIEM Systems]
SOAR --> EDR[EDR/XDR Solutions]
SOAR --> FW[Firewalls]
SOAR --> NAC[Network Access Control]
SOAR --> TIP[Threat Intelligence]
SOAR --> IAM[Identity Management]
SOAR --> CASB[Cloud Security]
SOAR --> EMAIL[Email Security]
SIEM -->|Alerts & Events| SOAR
EDR -->|Endpoint Telemetry| SOAR
FW -->|Network Events| SOAR
NAC -->|Access Events| SOAR
TIP -->|Threat Data| SOAR
IAM -->|User Context| SOAR
CASB -->|Cloud Events| SOAR
EMAIL -->|Email Threats| SOAR
style SOAR fill:#FF8000,stroke:#333,stroke-width:2px,stroke-dasharray: 5 5
The connection between SOAR and Security Information and Event Management (SIEM) systems is particularly crucial. While SIEM platforms excel at collecting and analyzing security data, SOAR enhances this capability by automating the response to identified threats. This integration creates a powerful feedback loop:
SIEM-SOAR Data Flow
Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) integration is another critical aspect of SOAR implementation. These tools provide detailed visibility into endpoint activities and threats, which SOAR can leverage to orchestrate targeted response actions.
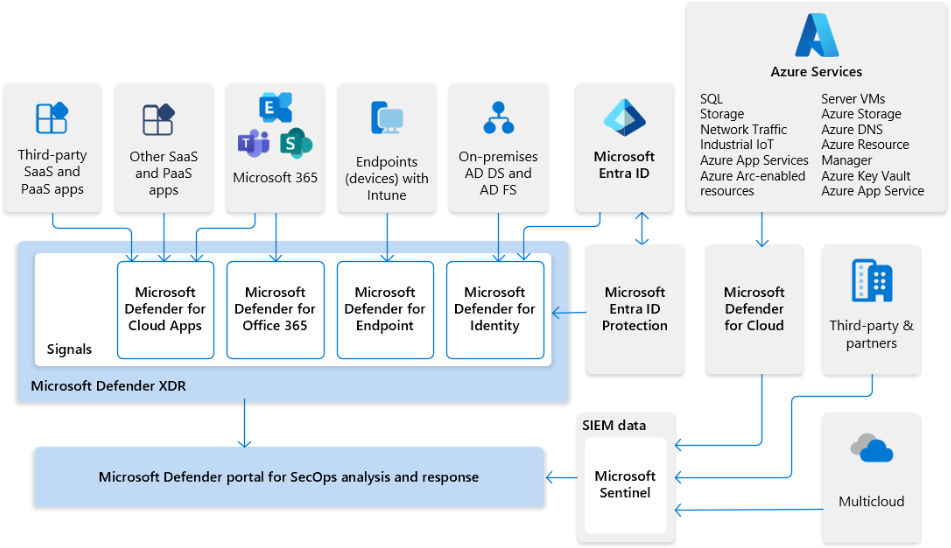
Firewall and network security tool orchestration enables SOAR platforms to implement network-based containment and remediation actions automatically. For example, when a compromised host is identified, SOAR can instruct firewalls to isolate that host from the network until remediation is complete.
Threat intelligence platform connections provide crucial context for security events. By enriching alerts with up-to-date threat intelligence, SOAR platforms can help security teams prioritize their response efforts and identify potential false positives.
In my work developing integrated security architectures, I've found that visual framework for ai safety principles can be applied to SOAR integration design. Using PageOn.ai's Deep Search capability has been invaluable for incorporating relevant integration diagrams into our security documentation, making complex technical relationships more accessible to all stakeholders.
The result of these integrations is a comprehensive security mesh—a connected ecosystem where each tool enhances the capabilities of the others, creating a security posture greater than the sum of its parts.
From Alert to Resolution: The SOAR Journey
Throughout my career in cybersecurity, I've observed that understanding the complete incident lifecycle is crucial for effective security operations. SOAR platforms provide a structured approach to this journey, from initial alert to final resolution. Let's visualize this process to better understand how SOAR transforms security response.
SOAR Incident Lifecycle
flowchart LR
Alert[Alert Generation] -->|Ingestion| Triage[Triage & Prioritization]
Triage -->|High Priority| Investigation[Automated Investigation]
Triage -->|Low Priority| Queue[Analyst Queue]
Investigation -->|Enrichment| Context[Context Gathering]
Context --> Analysis[Threat Analysis]
Analysis -->|Confirmed Threat| Response[Automated Response]
Analysis -->|Needs Review| Manual[Manual Analysis]
Queue --> Manual
Manual -->|Threat Confirmed| Response
Response --> Containment[Containment Actions]
Containment --> Remediation[Remediation Steps]
Remediation --> Documentation[Documentation & Reporting]
Documentation --> Closure[Case Closure]
style Alert fill:#ff9966,stroke:#333,stroke-width:2px
style Closure fill:#66BB6A,stroke:#333,stroke-width:2px
The journey begins with triage and prioritization—a critical step in managing the overwhelming volume of security alerts that organizations face today. SOAR platforms excel at this by applying consistent criteria to determine which alerts require immediate attention.
Alert Prioritization Matrix
Once prioritized, alerts enter automated investigation workflows that gather additional context and evidence. This might include checking threat intelligence sources, examining historical data, or collecting forensic information from affected systems.
Case management is another critical component of the SOAR journey. By maintaining comprehensive documentation of all actions taken, SOAR platforms create an audit trail that is invaluable for compliance purposes and for learning from past incidents.
In my experience leading security operations teams, I've found that ai strategy principles can be applied to SOAR implementation to create more intelligent and adaptive response capabilities.
Creating end-to-end response visualizations with PageOn.ai's AI Blocks has helped my team better understand and optimize our incident response processes. These visualizations make it easier to identify bottlenecks, redundancies, or gaps in our workflows, leading to continuous improvement in our security operations.
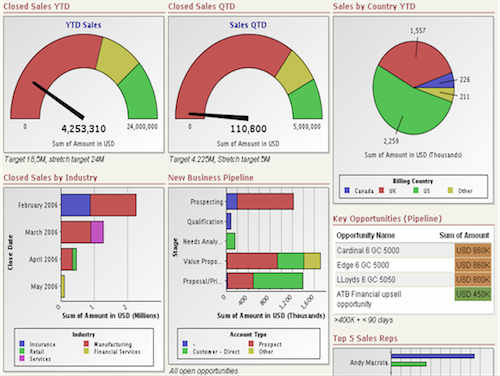
Measuring SOAR Success: Metrics That Matter
Throughout my career implementing security automation solutions, I've learned that measuring the success of SOAR platforms requires a comprehensive set of metrics that capture both operational efficiency and security effectiveness. Let's explore the key performance indicators that provide meaningful insights into SOAR performance.
SOAR Impact on Response Metrics
Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) are perhaps the most critical metrics for evaluating security operations effectiveness. In my experience, SOAR implementations typically achieve:
- 75-85% reduction in MTTD by automating alert triage and prioritization
- 60-80% reduction in MTTR through automated investigation and response actions
- 200-300% increase in the number of incidents that can be handled without adding staff
- 50-70% reduction in false positives requiring analyst attention
Creating effective executive dashboards is essential for communicating SOAR value to leadership. I've found that focusing on business outcomes rather than technical metrics is most effective:
ROI calculation for SOAR initiatives should consider multiple factors, including:
SOAR ROI Components
- Reduced personnel time spent on routine tasks
- Faster incident resolution leading to decreased breach impact costs
- Improved compliance posture and reduced audit findings
- Increased capacity to handle security events without additional staffing
- Reduced alert fatigue and analyst burnout, leading to better retention
In my experience leading security teams through digital transformation, I've seen how AI tool trends 2025 are already influencing the evolution of SOAR platforms, with more intelligent automation and predictive capabilities on the horizon.
Using PageOn.ai to transform complex security metrics into clear visual narratives has been invaluable in my work with executive stakeholders. These visualizations help bridge the gap between technical security operations and business outcomes, making it easier to justify continued investment in security automation.
Implementation Strategies: From Selection to Deployment
Based on my experience implementing SOAR solutions across various organizations, I've developed a strategic approach that maximizes adoption success while minimizing disruption. The journey begins with selecting the right SOAR platform for your specific needs.
SOAR Platform Comparison
When evaluating enterprise versus open-source SOAR options, I consider several factors:
| Consideration | Enterprise SOAR | Open Source SOAR (TheHive, Shuffle) |
|---|---|---|
| Initial Cost | High (licensing) | Low (infrastructure only) |
| Maintenance | Vendor supported | Internal resources required |
| Integration Breadth | Extensive pre-built integrations | Community-driven, may require custom development |
| Customization | Limited to vendor capabilities | Unlimited with development resources |
| Time to Value | Faster with pre-built content | Longer development cycle |
In my implementation projects, I've found that a phased approach yields the best results. This typically follows these stages:
SOAR Implementation Phases
flowchart LR
P1[Phase 1: Foundation] --> P2[Phase 2: Initial Use Cases]
P2 --> P3[Phase 3: Expansion]
P3 --> P4[Phase 4: Optimization]
P4 --> P5[Phase 5: Advanced Analytics]
style P1 fill:#FF8000,stroke:#333,stroke-width:2px
style P5 fill:#66BB6A,stroke:#333,stroke-width:2px
Successful SOAR implementation requires the right team structure and skills. In my experience, the ideal SOAR team includes:

Change management is perhaps the most overlooked aspect of SOAR implementation. Security analysts often worry that automation will replace their roles, when in reality it elevates their work by eliminating tedious tasks. I've found that involving analysts in playbook design and clearly communicating how automation will enhance rather than replace their expertise is crucial for adoption.
Looking ahead to AI tool trends 2025, I anticipate that SOAR platforms will increasingly incorporate machine learning to enhance decision-making capabilities and automate even more complex security tasks.
Creating implementation roadmaps with PageOn.ai has been instrumental in my SOAR deployment projects. These visual guides help align stakeholders on priorities, timelines, and resource requirements, making the entire implementation process more transparent and manageable.
Future-Proofing Security Operations with SOAR
As I look ahead to the evolution of security automation, I see several emerging trends that will shape the future of SOAR platforms and security operations. The convergence of SOAR with artificial intelligence and machine learning capabilities is perhaps the most significant development on the horizon.

In my research and implementation work, I've identified several key areas where SOAR platforms are likely to evolve:
SOAR Evolution Timeline
Predictive response mechanisms represent one of the most exciting developments in SOAR technology. Rather than simply reacting to security events after they occur, next-generation SOAR platforms will leverage historical data and machine learning to predict and prevent threats before they materialize.
Predictive SOAR Response Model
flowchart TD
Data[Historical Security Data] --> ML[ML Training]
Telemetry[Real-time Telemetry] --> Analysis[Pattern Analysis]
ML --> Model[Predictive Model]
Analysis --> Detection[Anomaly Detection]
Model --> Detection
Detection --> Risk{Risk Assessment}
Risk -->|High Risk| Prevent[Preventive Actions]
Risk -->|Medium Risk| Monitor[Enhanced Monitoring]
Risk -->|Low Risk| Normal[Normal Operations]
Prevent --> Feedback[Feedback Loop]
Monitor --> Feedback
Normal --> Feedback
Feedback --> ML
style Model fill:#FF8000,stroke:#333,stroke-width:2px
Autonomous security operations represent the ultimate evolution of SOAR platforms. While human oversight will remain essential for strategic decisions and complex investigations, routine security operations will become increasingly autonomous. This shift will allow security professionals to focus on higher-value activities such as threat hunting, strategic planning, and security architecture.
However, this evolution comes with important limitations and considerations:
Limitations of Autonomous Security Operations
- Context understanding and nuanced decision-making remain challenging for AI systems
- Novel attack techniques may not be adequately addressed by automated systems
- Ethical considerations around automated actions that impact business operations
- Regulatory compliance requirements for human oversight in certain industries
- Potential for adversarial manipulation of automated security systems
In my work preparing organizations for next-generation security operations, I've found that using PageOn.ai's Agentic capabilities to model future scenarios has been invaluable. These visual models help security leaders anticipate changes in the threat landscape and plan their automation strategies accordingly.
The future of security operations lies in finding the optimal balance between human expertise and machine efficiency. SOAR platforms will continue to evolve, taking on more complex tasks and making more sophisticated decisions, but always within a framework of human governance and oversight.
Transform Your Security Operations with PageOn.ai
Create stunning visual representations of your security architecture, automation workflows, and incident response processes. Make complex security concepts clear and actionable for all stakeholders.
Start Creating with PageOn.ai TodayConclusion: The Future of Automated Threat Response
Throughout this exploration of SOAR platforms and automated threat response, I've shared my insights on how these technologies are transforming security operations. From the evolution of security response frameworks to the future of AI-enhanced automation, it's clear that SOAR represents a critical capability for modern security teams.
As security threats continue to evolve in sophistication and scale, the need for efficient, consistent, and effective response mechanisms becomes increasingly important. SOAR platforms provide the foundation for meeting this challenge, enabling security teams to do more with less while improving their overall security posture.
In my experience implementing and optimizing security automation solutions, I've found that visualization is key to success. Clear visual representations of complex security architectures, workflows, and processes help bridge the gap between technical practitioners and business stakeholders, facilitating better communication and alignment.
This is where tools like PageOn.ai become invaluable. By transforming complex security concepts into clear, compelling visuals, PageOn.ai helps security leaders communicate more effectively, train their teams more efficiently, and drive better security outcomes across their organizations.
You Might Also Like
How AI Saves Marketing Teams 5+ Hours Weekly While Boosting Productivity 83% | Visual Content Revolution
Discover how AI transforms marketing workflows, saving 5+ hours weekly and boosting productivity by 83%. Learn visual content strategies that eliminate manual tasks and accelerate campaigns.
Visualizing the AI Revolution: From AlphaGo to AGI Through Key Visual Milestones
Explore the visual journey of AI evolution from AlphaGo to AGI through compelling timelines, infographics and interactive visualizations that map key breakthroughs in artificial intelligence.
The Science Behind Success: How AI-Powered Content Creation Delivers 25% Higher Success Rates
Discover why AI users report 25% higher content success rates. Learn proven strategies, productivity gains, and competitive advantages of AI-powered content creation.
Prompt Chaining Techniques That Scale Your Business Intelligence | Advanced AI Strategies
Master prompt chaining techniques to transform complex business intelligence workflows into scalable, automated insights. Learn strategic AI methodologies for data analysis.
